Thats the most cost effective. SSLTLS Scanner on HTTPS ports if needed.

Hacking Your Home Pen Testing Your Local Network By Aliaksandra Havia Medium
First of all you can try to get a technical friend to help.

. Advanced IP Scanner is one of the programs that undoubtedly supports this fundamental step of Network PenTesting. SMishing realistically only has two attack vectors for a pentester. Expect to find only the ports you know you have explicitly opened open.
Based on the results start the Network Vulnerability Scan with OpenVAS and check for open ports. This step is very helpful in case your VM gets corrupt. I Pick which exploit to use.
First run a full scan against your home IP address. 2 More posts from the AskNetsec community 36 Posted by 5 days ago. Check out the PTES standards section on network reconenum and try those techniques.
Here are a few security tools you can use to conduct pentesting for your network systems. Otherwise as long as you have a firewall properly configured and believe the game software itself wont be attacked you are good. See How to extend a Home Network Home Router Setup.
If you dont know any such person then grab a trusted friend who is non-technical and ask them to. How To Perform A Successful Network Penetration Test Purplesec How To Perform A Successful Wifi Penetration Test Building A Test Lab For Pentesting Guide White Oak Security Firewall Penetration Testing Steps Methods Tools Purplesec Hacking Your Home Pen Testing Your Local Network By Aliaksandra Havia Medium. It is free compatible with Windows 10 and does not require complicated installation and use processes.
This step is very helpful in case your VM gets corrupt. First run a full scan against your home IP address. The Lovebox has an interesting way of accomplishing this.
After your organization has developed a strategy for the network pentest its time to initiate reconnaissance. While youre examining your network traffic you should look for Link-Local Multicast Name Resolution LLMNR and ensure that its disabled if possible. You can extend your home network by.
Then verify that it is your home router that is performing the filtering and not your ISP. CNAME Makes the domain name to another domain name. The first thing they are going to do is port scan your IP address and find out what youve got running if anything.
Also to bypass any potential administrating issues be sure to right click on the Command Prompt icon and select Run as Administrator. If you dont know any such person then grab a trusted friend who is non-technical and ask them to run a couple of small tests on your system. Ii Configure the exploit with remote IP address and remote port number.
Then verify that it is your home router that is performing the filtering and not your ISP. Ad Een pentest geeft u inzicht in de beveiligingsrisicos van uw bedrijf. OpenVAS UDP Full Scan top 1000 5.
Iv Configure the payload with local IP address and local port number. Threat modelling After collecting all the information you can about your target network its time to use this information for something dicey. To access the Command Prompt in Windows 10 type CMD into your desktop search field and it should come up.
Open ports are the key way for malicious hackers to gain unauthorized or backdoor access into a network and install malicious scripts. If you want to do a full but quick vulnerability scan try a scan template that runs multiple tools at the same time. OpenVAS TCP Full Scan ports 1-65535 4.
Expect everything else to be filtered. Iii Pick a payload. Just run and go.
Nessus vulnerability scanning tool used for vulnerability assessment VA process Nmap network discovery and security auditing tool NetCat port scanning and listening tool used to read and write in a network. All of these utilities can be accessed from the Windows Command Prompt. When you first plug the device in and open the lid it creates a new WiFi network.
UDP Scanner top 1000 ports 3. Disable the Windows Firewall. The first thing they are going to do is port scan your IP address and find out what youve got running if anything.
Ii Configure the exploit with remote IP address and remote port number. To connect the network you must type the username and click connect. Those exploits would need to run over the port you have open.
While replies to SMishing attempts may reveal sensitive information links front-ending fake authentication pages tend to work best when trying to exploit users. Replying to a text or clicking on a link. Based on that vast experience the following are three tips for how to improve scoping your pentests.
Creating a clone of it will prevent you from re-installing it again and again. In my work with Cobalt and their variety of different customers Ive seen several ways to scope a network pentest as well as the impact these methods have had on testing results. Understand the Customers Priorities.
The first thing we need to do is connect the box to a WiFi network. If youre not running anything and all ports are closed the attack is basically done unless there is a super critical known vulnerability unpatched on your edge router the chances of getting in with no ports open is extremely low. First have them try to get on your.
You can create a clone by Right clicking on the Virtul machine instance in VBox and click on clone You will notice that a cloned virtual WinXP will be created for you. To do this open a port on your router and rerun the scan. Ii Configure the exploit with remote IP address and remote port number.
To connect the network you must type the username and click connect. Disable the Windows Firewall. Advanced IP Scanner is one of the programs that undoubtedly supports this fundamental step of Network PenTesting.
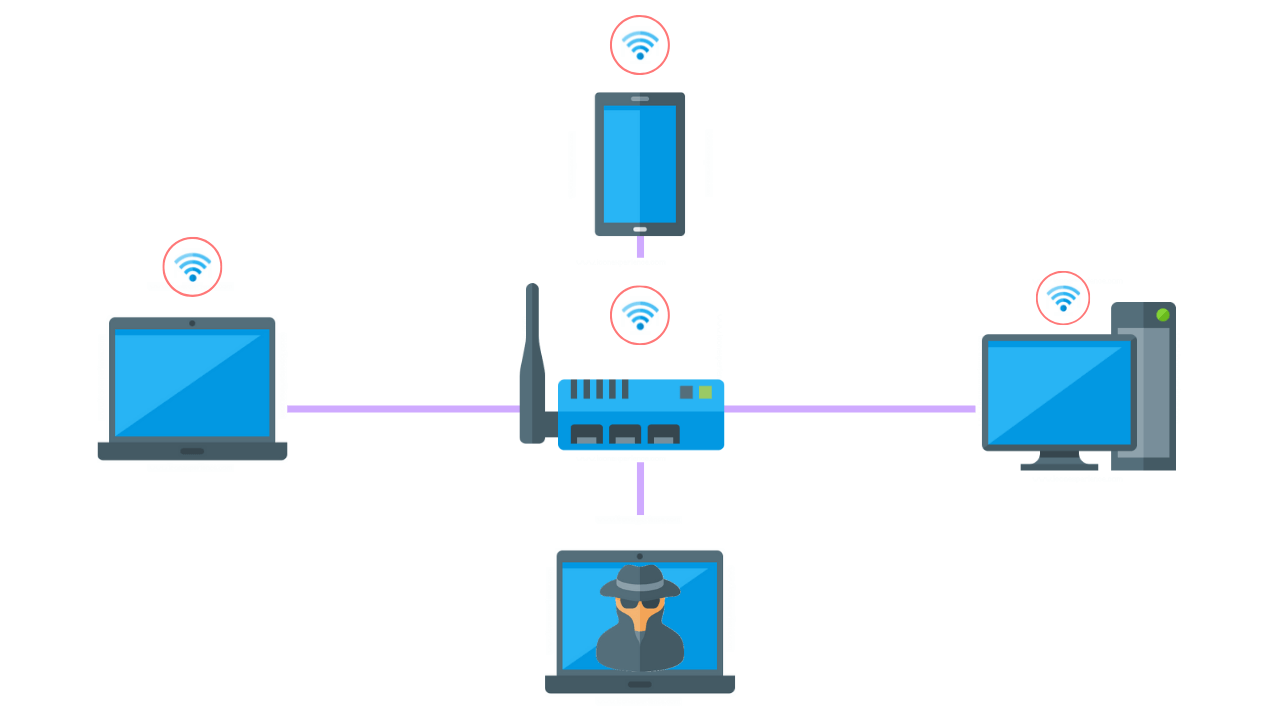
How To Perform A Successful Wifi Penetration Test

Firewall Penetration Testing Steps Methods And Tools That Work
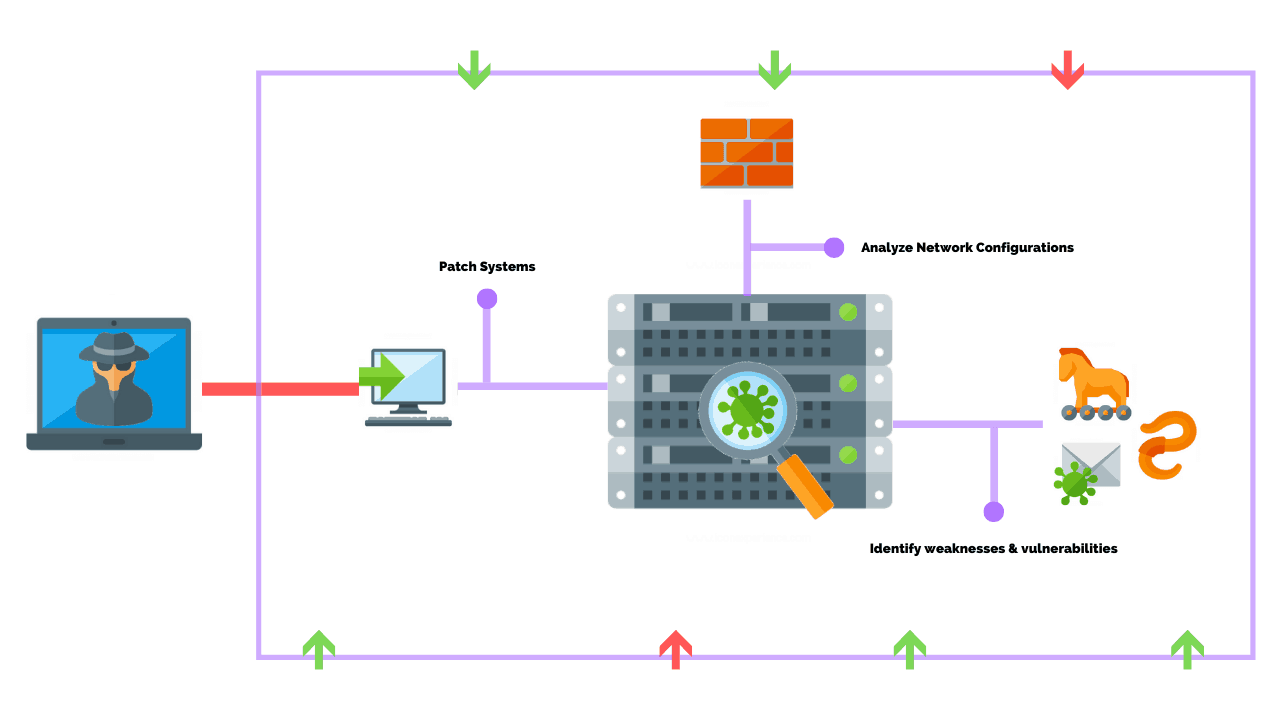
How To Perform A Successful Network Penetration Test Purplesec

How To Make Your Network Secure The Basics Networking Infographic Computer Security Cyber Security Education

Ultimate Guide On How To Perform A Successful Network Penetration Test

How To Scope A Network Penetration Test Pentester Tips Cobalt

0 comments
Post a Comment